When working with an unfamiliar VMware environment, especially in the consulting field, you may run into a scenario where you need to use the out-of-band management system of a host and cannot find any information on the IP configuration. Maybe the client doesn’t have documentation or maybe you’ve been hired to do the documentation for them. Luckily, if you’re faced with this dilemma, there is an easy way to look up this information using PowerCLI without having to take the host down to get into the BIOS. However, you’ll need to fulfill the following requirements:
- PowerShell 2.0 or higher must be installed on the client connecting to the ESXi hosts
- PowerCLI 4.0 or higher must be installed on the client connecting to the ESXi hosts
- Port 443 must be open from Client to ESXi hosts
The fastest and most efficient way to obtain the information we need is to use a PowerShell script written by Carter Shanklin. Carter has already done the heavy lifting for us and created a PowerShell function that allows us to query our ESXi hosts for the information. You can download the script here, or copy and paste the contents from below into a notepad and save it as a .ps1:
function Get-VMHostWSManInstance {
param (
[Parameter(Mandatory=$TRUE,HelpMessage="VMHosts to probe")]
[VMware.VimAutomation.Client20.VMHostImpl[]]
$VMHost,
[Parameter(Mandatory=$TRUE,HelpMessage="Class Name")]
[string]
$class,
[switch]
$ignoreCertFailures,
[System.Management.Automation.PSCredential]
$credential=$null
)
$omcBase = "http://schema.omc-project.org/wbem/wscim/1/cim-schema/2/"
$dmtfBase = "http://schemas.dmtf.org/wbem/wscim/1/cim-schema/2/"
$vmwareBase = "http://schemas.vmware.com/wbem/wscim/1/cim-schema/2/"
if ($ignoreCertFailures) {
$option = New-WSManSessionOption -SkipCACheck -SkipCNCheck -SkipRevocationCheck
} else {
$option = New-WSManSessionOption
}
foreach ($H in $VMHost) {
if ($credential -eq $null) {
$hView = $H | Get-View -property Value
$ticket = $hView.AcquireCimServicesTicket()
$password = convertto-securestring $ticket.SessionId -asplaintext -force
$credential = new-object -typename System.Management.Automation.PSCredential -argumentlist $ticket.SessionId, $password
}
$uri = "https`://" + $h.Name + "/wsman"
if ($class -cmatch "^CIM") {
$baseUrl = $dmtfBase
} elseif ($class -cmatch "^OMC") {
$baseUrl = $omcBase
} elseif ($class -cmatch "^VMware") {
$baseUrl = $vmwareBase
} else {
throw "Unrecognized class"
}
Get-WSManInstance -Authentication basic -ConnectionURI $uri -Credential $credential -Enumerate -Port 443 -UseSSL -SessionOption $option -ResourceURI "$baseUrl/$class"
}
}
# Examples (make sure you are connected to an ESX server.)
# Get-VMHostWSManInstance -VMHost (Get-VMHost) -class CIM_Fan -ignoreCertFailures
# Get-VMHostWSManInstance -VMHost (Get-VMHost) -class VMware_Role -ignoreCertFailures
# Get-VMHostWSManInstance -VMHost (Get-VMHost) -class OMC_Card -ignoreCertFailures
# See http`://www.vmware.com/support/developer/cim-sdk/smash/u2/ga/apirefdoc/ for a list of classes.
The Details Behind the Script
Before using any old PowerShell script from the internet, it’s always good to look it over and understand it. So, I’m going to take a second and explain how this script works.
Remote PowerShell uses a communications protocol called WS-MAN which stands for “Web Services for Management”. This protocol runs over HTTP or HTTPS, which is why we need port 443 open in order to use our script.
At the end of the script, we see the Get-WSManInstance cmdlet. This is the cmdlet that is used to query the host and return the information we are looking for. Basically, this entire function is just simplifying the input required to set up a WS-MAN connection to the host, which returns the resource information specified by the resource URI. The resource URI (Uniform Resource Identifier) is used to specify the type of resource. The format will look like the following if we are trying to get the IPMI information:
http://schema.omc-project.org/wbem/wscim/1/sim-schema/2/OMC_IPMIIPProtocolEndpoint
If we wanted to not use this script, we could just use Get-WSManInstance and take the time to type out all the required parameters. But we would also have to set up the credentials that allow us to connect to the host. This can be pretty tricky and tedious each time, which is why using Carter’s script is a much more efficient way. In one segment of the script, it will automatically dive into the properties of the host and run the AcquireCimServicesTicket method to create a one-time credential for remote connecting to the host.
In the example below, we will just query OMC_IPMIIPProtocolEndpoint to find the out-of-band information. This script can also be used to query other CIM classes of the host to obtain other information. To look up other CIM classes available, review VMware’s documentation.
Using Get-VMHostWSManInstance to Find the Out-of-Ban Information
After downloading the script, navigate to the location of the file. Hold Shift and Right Click on the file. Select Copy as Path:
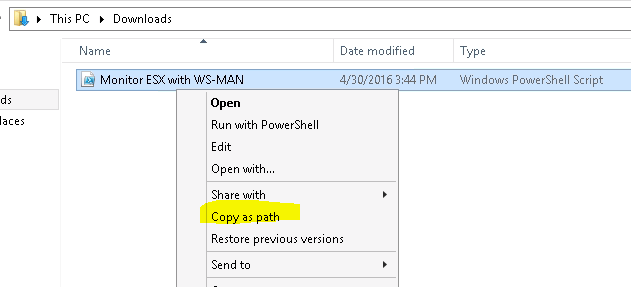
Quickly copy the path of the script
Open up a PowerCLI session. First, we need to import this function into our PowerShell session so we can run the function. To do this we’ll use Import-Module followed by the path to the script which we copied previously:
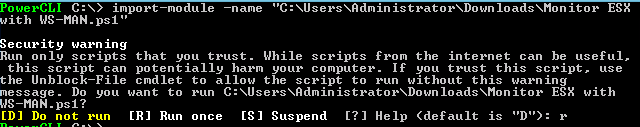
Import the script into our PowerShell session so we can easily run the function
Input “R” to import the script. You made need to adjust your execution policy setting depending on what they are currently at. After the script is imported, connect to your VCenter server or ESXi host using the following syntax:
Connect-VIServer –Server VC01
Get connected to a VCenter environment or a standalone ESXi host
Once connected, we can use our new function to query the host for the out-of-band management information. To do so we will use the –VMhost parameter with Get-VMhost to get the ESXi properties required to connect with WSMan, along with the class we are querying which in this case is going to be OMC_IPMIIPProtocolEndpoint. We’ll also include –ignoreCertFailures since we don’t care about the trusted cert, we are just querying information from the host. The syntax will look like the following:
Get-VMHostWSManInstance –Vmhost (Get-VMhost ESX01.tglab.lcl) –IgnoreCertFailures –Class OMC_IPMIIPProtocolEndpoint
After importing the script, the function is now available in our PowerShell session
We now get the IPMI information for our ESXi host, including the IP address configuration:
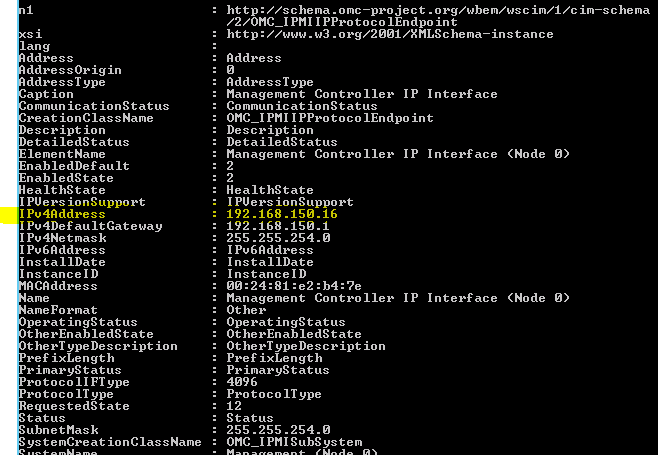
Out-of-Ban management information is returned
Finally, we can connect to the web interface of the IPMI controller and continue doing whatever task we needed to do. The best part about this is we can quickly get the information we need thanks to someone else doing the legwork to create and publish a script for everyone to use.
Comments/Suggestions?
I always recommend understanding the mechanics of PowerShell scripts so that you can customize them easily if they don’t fit your specific needs. That said, this takes a little bit of time but I’m sure it’s worth it in the long run. If you have any questions about this post let me know and I’ll help you out to the best of my ability. I love helping out the community and helping others as others have helped me 🙂
[the_ad id=”4738″][thrive_leads id=’18673′]








